London Lee Exploited vulnerabilities are a serious concern in today’s digital landscape. These exploits can compromise sensitive data, disrupt operations, and damage reputations. This article will delve into the intricacies of London Lee exploits, exploring their nature, potential impact, and most importantly, how to protect yourself and your organization from falling victim.
What are London Lee Exploits?
London Lee exploits generally refer to vulnerabilities discovered or utilized by individuals or groups associated with the name “London Lee.” While the name might suggest a specific individual or organized group, it’s crucial to understand that “London Lee” can be a pseudonym, a collective, or even a misattribution. The key takeaway is that these exploits target specific weaknesses in software, hardware, or even human behavior to gain unauthorized access or control. These vulnerabilities can range from zero-day exploits, leveraging unknown flaws, to exploiting known weaknesses that haven’t been patched.
The impact of a successful London Lee exploit can be devastating. Imagine your personal data, financial information, or confidential business documents falling into the wrong hands. This is the potential reality of these exploits. Furthermore, organizations can face operational disruptions, reputational damage, and significant financial losses due to data breaches and system compromises.
 Ví dụ về khai thác lỗ hổng London Lee
Ví dụ về khai thác lỗ hổng London Lee
Types of London Lee Exploits and Their Impact
London Lee exploits can manifest in various forms, including:
- Software Exploits: These target vulnerabilities in software applications, operating systems, or web browsers.
- Hardware Exploits: These focus on weaknesses in hardware components, such as firmware vulnerabilities.
- Social Engineering: This involves manipulating individuals to divulge sensitive information or perform actions that compromise security.
- Phishing Attacks: A common form of social engineering, phishing attacks often involve deceptive emails or messages designed to trick recipients into revealing credentials.
The impact of these exploits varies depending on the target and the specific vulnerability being exploited. Data breaches, financial losses, system downtime, and reputational damage are some of the potential consequences.
Protecting Yourself from London Lee Exploits
Protecting yourself and your organization from London Lee exploits requires a multi-layered approach. Here are some key strategies:
- Keep Software Updated: Regularly updating your software, operating systems, and applications is crucial for patching known vulnerabilities.
- Use Strong Passwords: Employ strong, unique passwords for all your accounts and avoid reusing passwords across different platforms.
- Enable Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone.
- Be Cautious of Phishing Emails: Be wary of suspicious emails, links, or attachments. Verify the sender’s identity and avoid clicking on links from untrusted sources.
- Educate Yourself and Your Team: Regular security awareness training can help individuals recognize and avoid potential threats.
How to Identify a Potential London Lee Exploit
Recognizing the signs of a potential London Lee exploit can be challenging. However, some red flags include:
- Unusual System Behavior: Sudden slowdowns, unexpected pop-ups, or unfamiliar programs running on your system could indicate a compromise.
- Suspicious Network Activity: Unexplained network traffic or unusual login attempts could be signs of an attack.
- Unexpected Account Activity: Monitor your accounts for any unauthorized transactions or changes to your settings.
What to Do if You Suspect You’ve Been Exploited
If you suspect you’ve been a victim of a London Lee exploit, take immediate action:
- Disconnect from the Network: Isolate the affected device from the network to prevent further damage.
- Change Your Passwords: Change passwords for all your accounts, especially those related to the compromised device.
- Scan for Malware: Run a full system scan using reputable anti-malware software.
- Report the Incident: Report the incident to the appropriate authorities, such as your internet service provider or law enforcement.
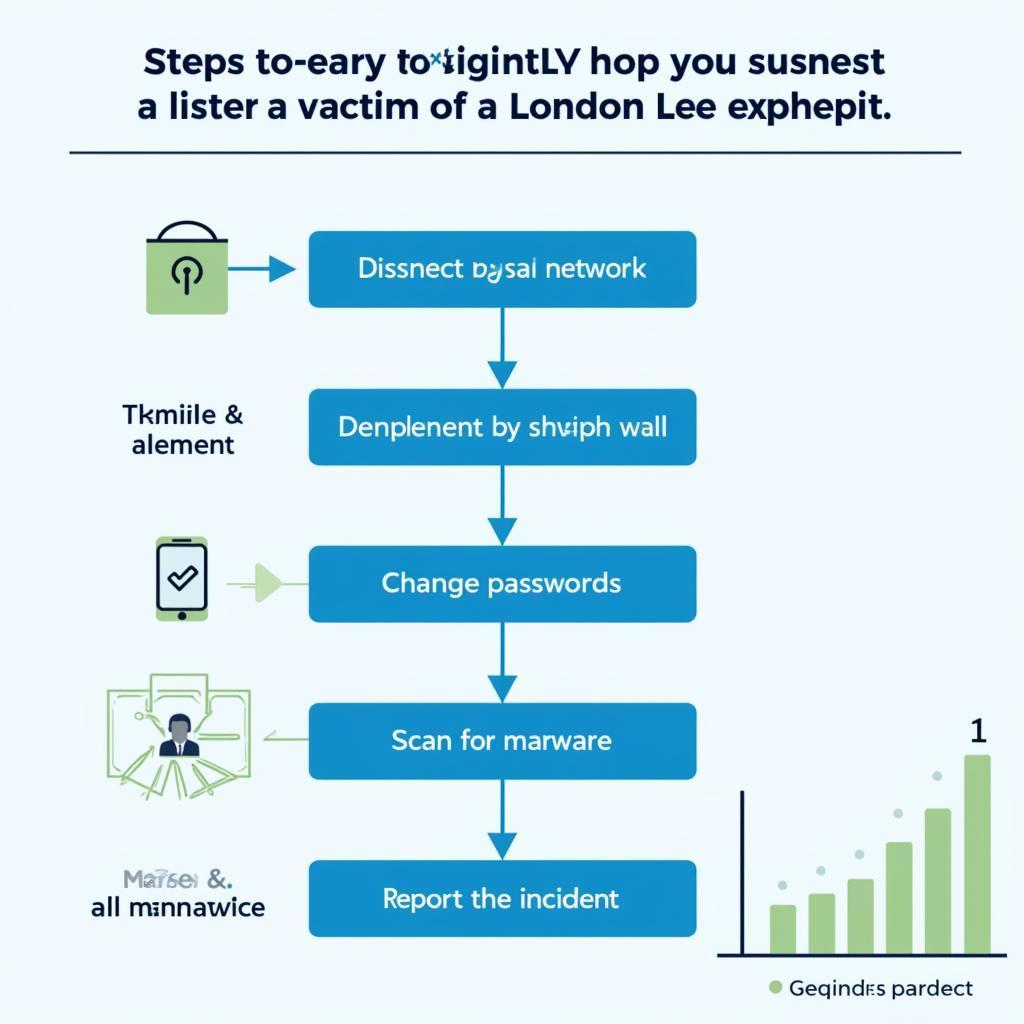 Quy trình ứng phó với khai thác lỗ hổng London Lee
Quy trình ứng phó với khai thác lỗ hổng London Lee
Conclusion
London Lee exploited vulnerabilities represent a persistent threat in the digital world. Understanding the nature of these exploits and implementing proactive security measures is essential for protecting yourself and your organization. By staying vigilant, keeping your systems updated, and educating yourself about the latest threats, you can significantly reduce your risk of falling victim to these attacks. Remember, vigilance is your best defense. Continue to learn and adapt to evolving threats to maintain a secure digital environment.
FAQ
- What is a zero-day exploit?
- How can I create a strong password?
- What is two-factor authentication and how do I enable it?
- How can I recognize a phishing email?
- Where can I report a cybercrime?
- What are some common types of malware?
- How often should I update my software?
Mô tả các tình huống thường gặp câu hỏi.
Người dùng thường thắc mắc về cách xác định xem họ có bị tấn công hay không, cách bảo vệ dữ liệu cá nhân và cách báo cáo sự cố. Chúng tôi luôn sẵn sàng hỗ trợ giải đáp mọi thắc mắc.
Gợi ý các câu hỏi khác, bài viết khác có trong web.
Bạn có thể tìm hiểu thêm về an ninh mạng và các biện pháp bảo vệ dữ liệu trên website của chúng tôi. Hãy tham khảo các bài viết về bảo mật mật khẩu, phòng chống phishing, và cập nhật phần mềm.